
Has your system been compromised?
Yes. You…
Your computer is hacked. You are being used. You are BOTNET.
Shutting down.
Just kidding! Your computer clearly isn’t shutting down, and we can’t say for sure whether or not your computer is actually hacked…
It’s the kind of thing most people don’t worry about on a daily basis–the security of their computer. Just like you probably don’t think about the security of your video game accounts. Hopefully, the game’s developers are.
Gaming Industry is a Big Target for Theft and Fraud
Everywhere you go on the internet to read about games, you’ll find mention of how it’s a $100 billion dollar industry. That’s an impressive amount of money. That kind of loot hoard draws the nefarious types out from their gloomy caverns and twisty, conniving towers.
See, that money doesn’t just come from game purchases. It also comes from in-game purchases.
And, in order to make purchases in a game, you need to pay with money. This means you’re connecting some kind of payment account, like a credit or debit card. It also means you’re verifying your identity by providing identifying information:
- Home address
- Email address
- Phone number
- Your name
You’re also setting up a username and a password. And who knows how many places you use the same password?
If a fraudster gets his or her hands on that information, it could be game over for you and your credit card limit.
 That information can be used to make purchases or sold out to other nefarious companies for who knows what.
That information can be used to make purchases or sold out to other nefarious companies for who knows what.
If you’re a game developer and you’re incorporating an in-game store, that uses real money, you need to think about security.
If you’re a game developer that simply requires players to log in (say, through Facebook or Google), then you still need to think about security. Identifying personal information and account credentials is still valuable to those who would do evil.
The Big BOTNET Threat

One of the most common attacks made against online games is DDOS attacks.
DDOS stands for distributed denial of service.
Apparently, these attacks are really easy to perform. That’s part of the reason why you’ve probably heard of them before–they’re fairly common.
In order to perform a DDOS attack, the villains need a BOTNET. A BOTNET is a group of networked computers.
Hackers will send virus downloads (like email spam) and wait for users to open the virus on their computers. Once that happens, the malware is installed on the computer and essentially makes the computer a robot slave.
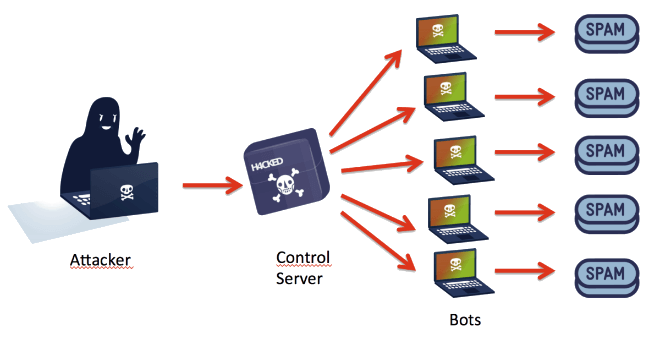
Any hacked system becomes a remote-controllable minion of the DDOS army. Most of the time, users won’t even notice they’ve been hacked.
Once the hacker (known as a BOT herder) amasses a big enough computer slave army, they can initiate an attack.
The attack consists of ordering the BOTNET to access a specific IP or website, all at once. This enormous wave of requests is too much for the target site to handle. First, traffic to the site slows down. Then the site starts dropping connections.
Finally, the site is so overloaded it cracks under the pressure and shuts down.
BOTNETS average around 20,000 computer slaves. The largest one had 30 million.
DDOS attacks are pretty easy. Because, unfortunately, the insidious few who want to use BOTNETS don’t even need to set up their own. There are allegedly websites that make it easy for any user with an account to take advantage of existing BOTNETs. All they need is the coding, which these websites deliver.
In a funny twist, DDOS attacks aren’t always malicious (or even attacks). Sometimes the content is so good that people overload the servers innocently as they all try to access the page around the same time. It’s good-intentioned server overload.
The Real Threat
The DDOS attacks in and of themselves aren’t totally harmful. Eventually, the system can recover.
Usually, these attacks are a distraction, so that hackers can enter the system while tech support deals with the downed servers.
While everyone is distracted, the hackers scrape information (credit cards, home addresses, login credentials, users’ names, etc.) and get out before anyone notices.
This kind of hack can take weeks of investigation before the hacked company realizes data has been compromised.
Case and point: Sony
Sony’s Battle With PSN Hacks

2011 was a dark year for all gamers with an account on the PlayStation Network and finally proved the superiority of XBL (JK, Xbox Live gets hacked too).
What happened? The personal data of over 77 million PSN users, logged in Sony’s database, was compromised by hackers.
It was significant for a few reasons.
One: 77 million people is a huge breach. It was the biggest security hack to hit consoles at the time…and it might still hold that title.
Two: The PSN service was pulled offline for 3 weeks…which is a huge amount of downtime. Three weeks without online capabilities!
Three: It was a targeted attack–an act of retribution from Anonymous.
Four: It took days for Sony to discover that information had been stolen and alert their user base: names of users, email addresses, birth dates, home addresses, PSN passwords–it was all swiped.
PSN: Hack at it Again
 In 2017, Sony had another attack on their PSN, allegedly. The culprit was a group called “OurMine” who admitted their involvement (and broke the news) via Sony’s PlayStation Brasil twitter account. To quote OurMine’s tweet, they “are a security group.”
In 2017, Sony had another attack on their PSN, allegedly. The culprit was a group called “OurMine” who admitted their involvement (and broke the news) via Sony’s PlayStation Brasil twitter account. To quote OurMine’s tweet, they “are a security group.”
Their shtick is hacking into big businesses and exposing those weaknesses to land a job. OurMine tweeted “if you works [sic] at Playstation then please go to our website ourmine.org -> Contact”.
The group alleged they stole information from the PSn database, but they claimed they were never going to share the information. They were only going to show it to Sony to prove they did it.
It doesn’t seem to have worked and didn’t have the same kind of backlash that the 2011 hack had.
The Effects of Security Breaches
Sony estimated that it would lose about $171 million USD after the hack and the PSN’s extended offline period. While they returned online functionality after a few weeks, the PlayStation store stayed offline for months.
With a breach like this, a few things happen:
- Consumer trust erodes
- The company brand is damaged
- Players leave (or can’t play)
- Players stop buying (or can’t buy)
These outcomes go hand-in-hand with lacking security.
They aren’t always crippling–none of the breaches/hacks stick around for long, consider the success of the PS4.
In an effort to earn back consumer trust and operate in good faith, Sony doled out some free games to players after the incident was cleared up. They also implemented extra security measures, encouraged users to change their passwords, and even offered security monitoring.
All these remedies netted Sony that estimated a $171 million dollar price tag.
That is an expensive fix. But it seemed to work, and Sony’s PlayStation is still popular today, surviving a few more episodes of turmoil on the security front.
My Account is Stolen!
Stealing accounts is another way nefarious types can undermine the fun of gaming and also turn a substantial profit.
Weapon skins in games like Counter-Strike have real-world value. Weapons and gear in games like World of Warcraft have real-world value, as does the currency in those games.
There are rules in most of these games that prohibit selling items or the currency outside of the game. But, people do it anyway. And it’s lucrative.
Instead of setting up farming bots (which is something people do when they’re looking to profit from selling in-game resources outside of the game), hackers will actually steal player accounts.
They steal the account info through malware, then lock the player out of the account by changing the password. From there, the player’s top-tier gear is sold or moved to another account owned by the hacker to sell later.
If the original user does regain control of their account, they’ll usually log in to find everything gone. Accruing top-tier gear in a game like World of Warcraft can take hundreds of hours and a healthy dose of luck during loot drops.
All of that time and effort can be undone in minutes if hackers get into player accounts.
Then it falls to the developer to conduct an investigation and determine if the player’s account really was hacked, and decide how to restore the player’s old gear.
Account hacking isn’t affecting 70 million players in a single afternoon, but the players that do get hacked have it pretty bad. That’s without considering that credit cards could be tied to the account for in-game purchases, which the hacker now has access to.
The more accounts that are hacked, the less you have real players playing the game. How you handle a stolen account will determine whether or not you retain a high-level player in your game. The accounts that hackers go after are the ones with hundreds of hours of game time and all the best gear–aka some of the game’s “best” players.
Not from a skill standpoint (though that may be the case), but from a valuable-to-the-studio standpoint. These players are part of the reason devs made the game in the first place.
Protecting against hacking preserves the integrity of the game. Players don’t want to play an MMO with a bunch of hacked farming characters. And they don’t want to have to worry about their own account being hacked.
Unfortunately, it doesn’t even take a hack to get to these accounts. Some players will just leave themselves logged in on a public computer, without even thinking about it. Bye-bye, loot!
Fraud so Big the Feds Had to Handle It
Time for another real-life story.
FIFA coins, fraud, four arrests, and a death.
Four men used modified Xbox One consoles and some clever code to trick the FIFA game into thinking they had played thousands of games on their accounts.
The more games you play, the more FIFA coins you earn. The more coins you earn, the more football players you have access to the water heater.
But these guys weren’t using the coins themselves…
They were mining these coins and selling them to willing buyers. They made around $16 million dollars before the FBI stepped in and shut it down.
This is an interesting case because the four men who got in trouble (three pled guilty, one went to court and was convicted, and then passed away around his 27th birthday before he could appeal the ruling) weren’t trying to use the coins to give themselves an unfair advantage (in the game, anyway…maybe in life!).
But, they did change the game by bringing so many coins to market and making them available. And they used pirated code to pull off the whole money-making scheme.
You’ll always have players who are willing to cheat, and these four men gave the cheaters the opportunity to do so. FIFA can’t have that in the game because it will put the players who don’t buy coins (the ones playing by the rules) at a disadvantage.
It wasn’t a game-ruining hack. It didn’t involve stealing other accounts, or hacking information. But it’s still fraud.
Protect Your Game Against Fraud and Theft

Unfortunately, writing good code won’t cut it.
It doesn’t matter what genre your game is, or the audience you cater to. Any popular game is at risk. Popularity means the money-making potential for the swindlers.
The first step to prevent it is to be aware of it. Understand the threats, where they could come from, and what they look like when they unfold.
If you have a bigger project, consider looking into customized security solutions from a third party.
It’s good to have a plan in place. It’s also good to know that your plan might not work. Be ready to adapt.
If you do have a breach, be open and honest with your user base. Let them know as soon as possible if their information has been compromised.
You’re in this business to make games, not protect the world from villains…Sometimes, you’ll have to do both!
